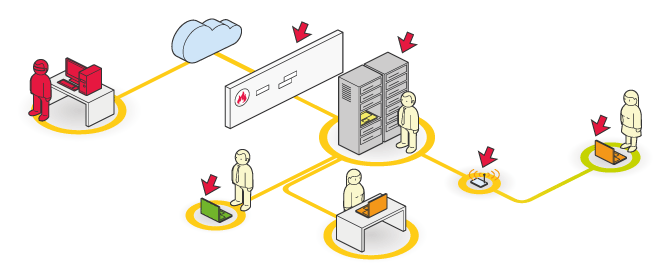
Risks :
A computer network attacker regularly seeks defects in a site’s configuration, a server, or a laptop to get into the company’s computer network.
Objectives :
The audit of computer security configuration is aimed at several specific points :
-
Discovering the configuration inaccuracies in database or web servers.
-
Identifying problems due to the obsolescence of certain embedded software (“firmware”) meant for the management of routers and other computer network components.
Therefore a true “revision” of the configuration files and the rules implemented in numerous information system components (router, Firewall, IDS, HTTP, etc.) can be achieved.
Each of these information system blocks will be hardened to deal with the most commonly encountered cyber attacks in a corporate network.
Note: The blocks presented in the categories of web service, modules, and database introduce the technologies that we have capitalised on and created specific audit tools.
Reports :
Configuration audit report and correction tools
Maturity :
- Discover the other existing maturity levels in our catalogue.