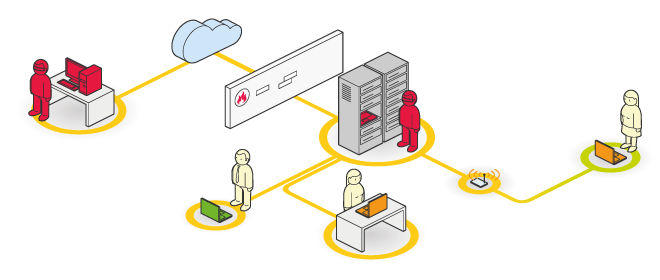
Risks :
The use of networks or applications connected to the Internet exposes the company to risks of cracking, misuse of information, and destruction of vital company data.
Objectives :
This audit simulates an intrusion targeting the company’s information system, and the action radius of this mission may be limited. However, it is possible to define the degree of penetration of our customers’ architecture.
The penetration test may originate internally, an approach that represents 80% of computer hacks (the malicious employee scenario). Or it may be external (the cracker scenario). It is thus possible to safely evaluate the information system’s level of risk against the ingenuity of an attacker. This approach also helps evaluate the reflexes of administration teams or contractors when faced with real threats.
The penetration test, because of its non-exhaustive nature, caters to customers wishing to thoroughly evaluate the uniquely technical aspects of a usually very limited perimeter. In the case of a significant perimeter engagement, like an information system or several Internet sites, it is better to move towards the test d’incursion involving a whole set of supplementary missions.
Our examination methods come from our technology watch and our R & D workshop. Some tools used in this phase were created by our security consultants. Therefore, this mission is sometimes composed of vulnerabilities that have not been published and are used in the form of “proof of concept,” directly related to an information system.
Thanks to the commitment of our company to respect people and employees, we reject all processes advocating social engineering.
Reports :
Penetration test report, risk visualisation tools, trophies.
Maturity :
This mission is at the highest level of maturity within our company. It has been performed at least 100 times with our customers. Our innovations regularly cause the mission to evolve, and we have also put a quality management procedure in place.
Evolution :
Beginning in 2013, we decided to create a new mission based on the penetration test, reinforced by additional components to respond to recurring risks that face 98% of our customers : the incursion test


