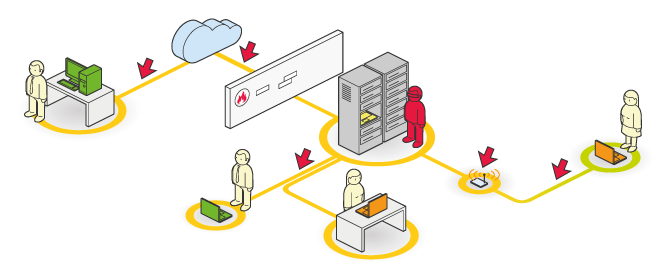
Risks :
The computer network, whether wired or wireless, can induce vulnerabilities in information system security. In addition, beyond the simple network media, the equipment dedicated to routing or filtering the stream can cause significant vulnerabilities that may strongly impact the applications or the services provided by the company.
Objectives :
The mission targeting the network portion is designed to discover the maximum vulnerabilities that may exist within the company’s network, the equipment, or network technologies that make it up.
In order to strengthen our offensive capabilities during our application penetration missions, we have capitalised on our skills within one of the first French penetration frameworks, Nemesis.

This technology makes up the auditor’s hand tools. Nemesis also allows for the comprehensive topology of a complex network made up of several thousand networks or types of equipment.
Maturity :
The mission has been performed at least 100 times with our customers. Our innovations regularly cause the mission to evolve, and we have also put a quality management procedure in place.
Remarks :
It is important to note that a configuration audit of some equipment, such as firewalls or routers, is the only mission that will allow comprehensive detection of computer vulnerabilities targeting the network media.


