Pycharm and computer security

For us, Eclipse was one of the flagship tools from our developments in Python, because it remains fast and flexible and is uses multiple languages. However, the latest developments in the PyCharm Professional Edition solution have changed our perception of the ideal tool.
In fact, PyCharm was transformed by drastically increasing processing speed and natively integrating many bricks, facilitating the development of computer security tools in Python.
Therefore, the last version of PyCharm 3.4.1 is based on version integration under various protocols like Git or even the use of development help tools, especially those based on PEP8.

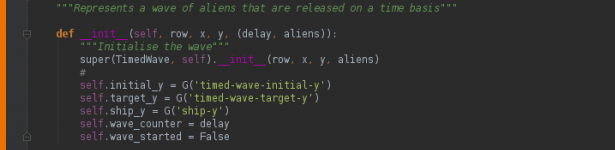
One of the key features in our use of PyCharm features is “remote debugging,” which allows us to simply and transparently integrate development within the very different and exotic operating systems of our development platforms.
We also discovered that the tool’s learning curve was very fast for novice users in Python. Therefore, a junior engineer in computer security can master and customize the tool in less than a week, which is not the case for the majority of development environments.
In addition, PyCharm natively supports GAE, SqlAlchemy, Pyramid, Web2py, Cython, Wxpython, PyQt, and PyGTK. So it allows us to support ourselves during our Python code audits on intelligent bricks, facilitating the understanding of software and audited libraries during our computer security missions.